DNS over HTTPS (DoH) support appeared on Windows 10 2004 build (May 2020 Update). Now Windows 10 can resolve names over HTTPS protocol using the built-in DoH client. In this article, we’ll tell what DNS over HTTPS protocol is used for, and how to enable and use it on the latest Windows 10 builds.
When your computer connects to a DNS server to resolve names, it sends and receives DNS requests/responses over the Internet in clear text. An attacker can intercept your traffic, detect what resources you have visited or manipulate your DNS traffic using a man-in-the-middle type of attack. The DNS over HTTPS protects user data privacy by encrypting all DNS queries. The DoH protocol encapsulates DNS queries into HTTPS traffic and sends them to a DNS server (you need use use a special DNS server with DoH support).
Windows 10 2004 doesn’t yet have a GPO parameter or an option in the graphic interface to enable DNS-over-HTTPS. Currently, you can only enable DoH on the latest Windows 10 builds via the registry:
- Run the
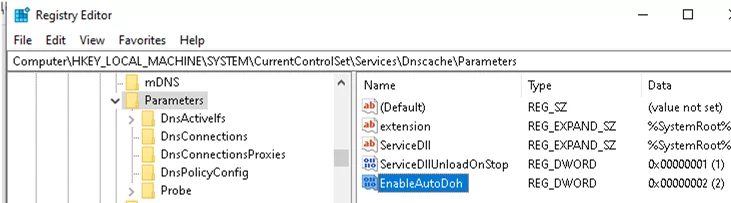
regedit.exe; - Go to the registry key
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Dnscache\Parameters - Create a new DWORD parameter with the name EnableAutoDoh and value 2;
You can also create this registry parameter using the New-ItemProperty cmdlet:
$EnableDNSoverHTTPSKey = 'HKLM:\SYSTEM\CurrentControlSet\Services\Dnscache\Parameters'
$EnableDNSoverHTTPSParameter = 'EnableAutoDoh'
New-ItemProperty -Path $EnableDNSoverHTTPSKey -Name $EnableDNSoverHTTPSParameter -Value 2 -PropertyType DWord –Force - Then restart the DNS client service. To do it, reboot your computer, since you won’t be able to restart the dnscache service normally (
Restart-Service -Name Dnscache –forcecommand returns the following error: Collection was modified; enumeration operation may not execute).
Then you will have to change the DNS settings of your network connection. You need to specify DNS servers with DNS over HTTPS support. Not all DNS servers support DoH yet. The table below shows a list of public DNS servers with DNS over HTTPS support.
| Provider | IP Addresses of DNS Servers With DNS over HTTP Support |
| Cloudflare | 1.1.1.1, 1.0.0.1 |
| 8.8.8.8, 8.8.4.4 | |
| Quad9 | 9.9.9.9, 149.112.112.112 |
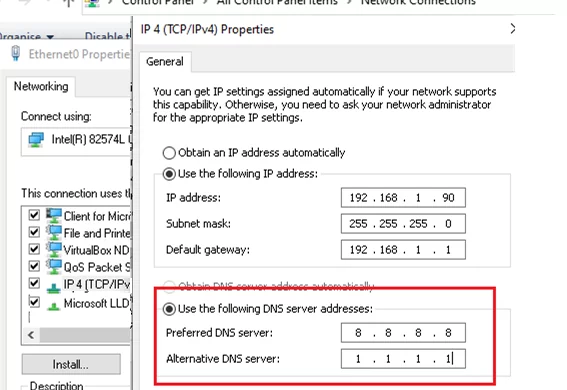
Open the network connection window (Control Panel -> Network and Internet -> Network and Sharing Center or ncpa.cpl). Then change the current DNS server IP addresses to the addresses of DNS servers that support DoH in the network adapter properties.
$PhysAdapter = Get-NetAdapter -Physical
$PhysAdapter | Get-DnsClientServerAddress -AddressFamily IPv4 | Set-DnsClientServerAddress -ServerAddresses '8.8.8.8', '1.1.1.1'
Then your DNS client will use HTTPS (443) protocol instead of standard UDP/TCP port 53 for DNS name resolution.
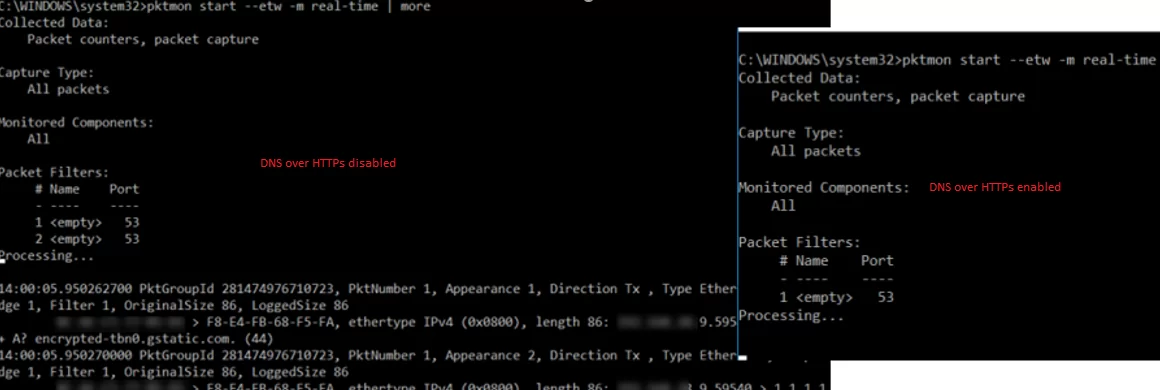
Using PktMon.exe, a tool to capture network traffic, you can make sure that no DNS requests are sent from the computer over 53 port.
Remove all current Packet Monitor filters:
pktmon filter remove
Create a new filter for the default DNS port (53):
pktmon filter add -p 53
Start real-time traffic monitoring (the traffic will be shown in the console):
pktmon start --etw -p 0 -l real-time
If you have configured DNS over HTTPS correctly, there will be no traffic on Port 53 (the screenshot below shows the console output with DoH enabled and disabled).
In the last year, DNS over HTTPS has been implemented in all popular browsers (Google Chrome, Mozilla Firefox, Microsoft Edge, Opera). You can enable DoH support in each of them. Thus, all DNS queries from your browser will be encrypted (DNS traffic of other apps will still sent as plain text).
DNS over HTTPS and DNS over TLS will create a lot of troubles for corporate network administrators since it will be harder to restrict access to external resources from internal networks.
9 comments
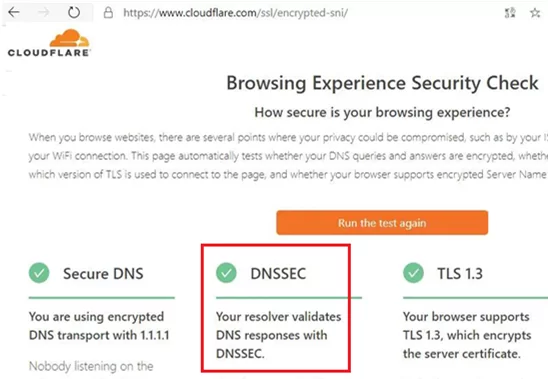
A correction to the last screenshot, DNSSEC is not the same as DNS-over-HTTPS. DNSSEC is for server-to-server, and DoT is for server-to-client. The Cloudflare web site is confirming that the Windows 10 is using DoT to communicate to its DNS resolver, and its DNS resolver has implemented the server-side DNSSEC features. The page is correct, you just need to highlight the Secure DNS box rather than the DNSSEC box.
Hello,
Thanks for your article. But It doesn’t work on my computer : there is always traffic on DNS port (53) even with a value of 2 for EnableAutoDoh, a good DNS (1.1.1.1) and after restart the computer.
Have you got an idea to resolve this ?
Thanks.
“Create a new DWORD parameter with the name EnableAutoDoh and value 2; ‘
Can we set this to 3 ???
Doesn’t work with 21H1 in case anyone is trying. Probably need to wait till next year for the Public builds to get this.
One question: Does the Windows Server 2022 DNS server support DNS over HTTPS (DoH)?
In an active directory network, all computers added to the domain have Active Directory DNS Server configured in the DNS client.
If I configure DNS over HTTPS (DoH) in the client but the Active Directory DNS Server does not support it …
You can only use DoH DNS client on Windows Server 2022:
DNS Client in Windows Server 2022 now supports DNS-over-HTTPS (DoH) which encrypts DNS queries using the HTTPS protocol. This helps keep your traffic as private as possible by preventing eavesdropping and your DNS data being manipulated. Learn more about configuring the DNS client to use DoH. https://docs.microsoft.com/en-us/windows-server/networking/dns/doh-client-supportWindows 10 does not support DNS over HTTPS and it doesn’t look like it ever will.
Very Good Post . It Solved My Problem After Changing Internet Connection.