Force Tunnel mode is enabled by default for all VPN connections in Windows (the ‘Use default gateway on remote network‘ option enabled in the VPN settings). In this mode, name resolution is performed using the DNS servers assigned to you by the VPN server, and you will not be able to resolve device names on your LAN.
There are two modes for VPN connections in Windows:
- Force Tunnel (Use default gateway option is enabled) – all traffic, including DNS, is sent to the VPN tunnel. In this mode, once you have connected to the VPN, you will not be able to resolve DNS hostnames on your local network (and cannot access the Internet through your LAN when the VPN is connected). You can only access local network resources by IP address (the client’s DNS cache partially helps in this case).I have found some recommendations for disabling the IPv6 protocol for your local (LAN) interface and it would be helpful if you want to use the Force-Tunneling mode.
- Split Tunnel (Use default gateway on remote network option is disabled) – in the VPN tunnel, only traffic destined for corporate servers is routed (according to the routing table). In this mode, Windows uses your local DNS servers for name resolution and ignores the DNS servers configured for the VPN connection. This means that your local network is used to access the Internet and resolve names (according to the LAN interface settings).
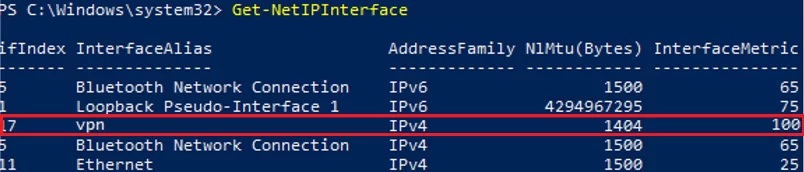
Windows 10/11 sends DNS queries from the highest priority network interface (with the lowest value of the interface metric). Run the PowerShell command to list the metrics of a computer’s network interfaces:
Get-NetIPInterface | Sort-Object Interfacemetric
There are two network connections on the computer:
- Ethernet connection with metric 25
- VPN connection with metric 100
This means that your DNS queries will be sent over the lower metric interface (Ethernet) to your local DNS servers, rather than to the DNS servers of the VPN connection. In this configuration, you will not be able to resolve names in the external VPN network.
Windows 10/11 automatically sets IPv4 metrics on network interfaces based on the speed and type of the interface:
| Connection speed and type | Default metric |
| Ethernet 1 GB | 25 |
| Ethernet 100 MB | 35 |
| Wi-Fi interface with 50-80 Mb speed | 50 |
(see the Explanation of the Automatic Metric feature for IPv4 routes https://support.microsoft.com/en-us/help/299540/an-explanation-of-the-automatic-metric-feature-for-ipv4-routes).
For example, you want to send DNS requests over a VPN connection. In our example, this means that you need to increase the metric of the local Ethernet adapter and make it greater than 100.
You can change the network interface metric either from the GUI or from the command line.
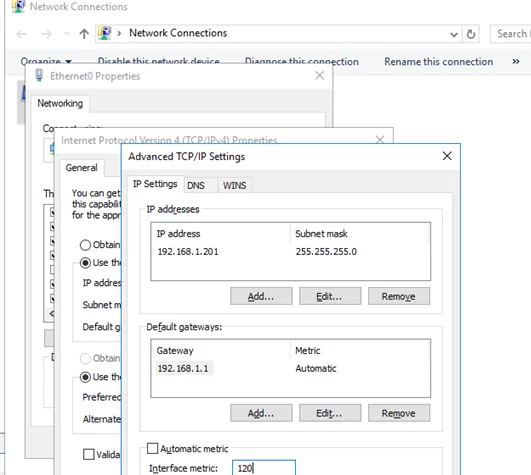
- Open the Network Connections control panel (
ncpa.cpl), open the properties of your Ethernet connection, select TCP/IPv4 properties, and go to the Advanced TCP/IP Settings tab. Uncheck the Automatic metric option and change the interface metric to 120. - You can also change the metric using PowerShell commands to manage network settings (specify the index of your LAN interface that you get by using the
Get-NetIPInterfacecmdlet):
Set-NetIPInterface -InterfaceIndex 11 -InterfaceMetric 120
Or with netsh (you must specify the name of your LAN connection):
netsh int ip set interface interface="Ethernet 3" metric=120
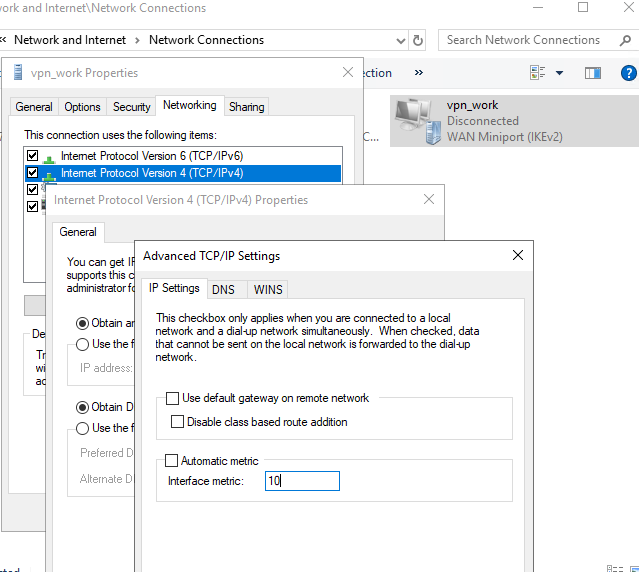
Similarly, you can reduce the metric value in the VPN connection properties.
In this configuration, DNS queries are performed over the VPN connection.
You can also change the settings of your VPN connection by changing the mode to SplitTunneling (DNS traffic goes to your LAN by default) and specifying the DNS suffix for the connection using PowerShell:
Get-VpnConnection
Set-VpnConnection -Name "VPN_work" -SplitTunneling $True
Set-VpnConnection -Name "VPN_work" -DnsSuffix yourdomainname.com
You can also specify which subnets’ traffic should always be routed to the VPN tunnel:
Add-VpnConnectionRoute -ConnectionName "VPN_work" -DestinationPrefix 172.16.15.0/24
Add-VpnConnectionRoute -ConnectionName "VPN_work" -DestinationPrefix 10.2.1.0/24
If you are using an OpenVPN Server, assign additional routes and DNS servers to clients using the following options:
push "route 10.2.2.0 255.255.255.0"
push "dhcp-option DNS 192.168.115.11"
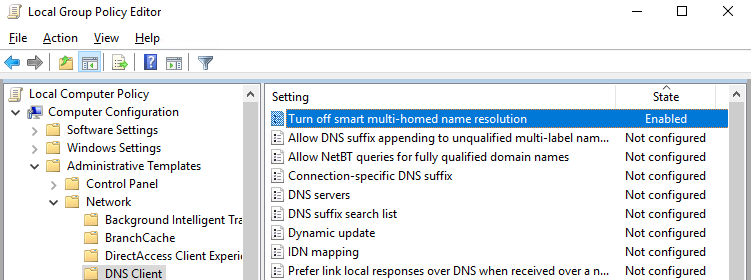
Note that the Smart Multi-Homed Name Resolution (SMHNR) feature is enabled by default in Windows 8.1 and up to Windows 1703. Windows sends DNS queries to all known DNS servers in parallel and uses a faster response if SMHNR is enabled. This is not secure, as external DNS servers (as specified in your VPN connection) may be able to see your DNS queries (DNS leak). To prevent DNS queries from being leaked, we recommend disabling SMHNR using Group Policy (Computer Configuration -> Administrative Templates -> Network -> DNS Client-> Turn off smart multi-homed name resolution = Enabled).
You can make the same changes directly to the registry using PowerShell commands:
Set-ItemProperty -Path "HKLM:\Software\Policies\Microsoft\Windows NT\DNSClient" -Name DisableSmartNameResolution -Value 1 -Type DWord
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\Dnscache\Parameters" -Name DisableParallelAandAAAA -Value 1 -Type DWord
6 comments
This deserves some love. Thanks for the help and the highly detailed explanation! This was driving me nuts!
It’s nice to hear that 🙂
Good stuff, have you noticed that you can also do something like below when adding the split tunnel routes.
Add-Vpnconnectionroute -Connectionname $ConnectionName -AllUserConnection -DestinationPrefix $Destination -RouteMetric 20
Worked in Win10 1904 but no longer in 2004. no error messages or anything but just no longer applies the metrics…
[…] Windows OS Hub – DNS Resolution via VPN Not Working on Windows 10 […]
“So changing the interface metric allows you to send DNS requests over the connection (LAN or VPN) where name resolution is the most priority for you.”. Now it’s not really true if SMHNR is on (Windows 10 – 2004). If SMHNR is enabled, system send request over all interfaces. System doesn’t use the response it received first. System uses the DNS response depends on interface metric.
Good work! Just what I was looking for to send DNS lookups up the VPN connection on a Windows 11 PC where you can’t seem to get to the Advanced TCP/IP settings GUI anymore. Worked it into a PowerShell script:
$ifIndex = Get-NetIPInterface | where-object { $_.InterfaceAlias -EQ $ConnectionName } | Select -Expand ifIndex
Set-NetIPInterface -InterfaceIndex $ifIndex -InterfaceMetric 10